Ethical Hacking Nptel Week 3 Assignment Answers
Are you looking for Ethical Hacking Nptel Week 3 Assignment Answers? You’ve come to the right place! Access the latest and most accurate solutions for your Week 3 assignment in the Ethical Hacking course.
Table of Contents

Ethical Hacking Nptel Week 3 Assignment Answers (July-Dec 2025)
Question 1. Which of the following statement(s) is/are false?
a) IP protocol uses connection-oriented routing.
b) IP protocol uses connection-less routing.
c) In connection-less routing, each packet is treated as an independent packet.
d) None of these.
Question 2. A routing table entry that is manually configured remains unchanged unless manually modified is called a ______ routing table entry.
a) Automatic
b) Static
c) Dynamic
d) None of these
Question 3. Which of the following statements is/are false about direct and indirect packet delivery?
a) Direct delivery happens within the same network.
b) Indirect delivery is used for different networks.
c) In indirect delivery, packets travel through multiple routers.
d) None of these.
Question 4. Which of the following statements correctly describe features of dynamic routing?
a) All routers are manually configured by the network administrator.
b) Routing table updates periodically depending on the network condition.
c) Routers exchange control information, which consumes network resources.
d) It can automatically find alternate paths during link failures.
e) It never changes the routing table once initialized.
Question 5. In the routing table, which of the following flags indicates that the route uses a gateway to reach the destination?
a) U
b) G
c) H
d) D
e) M
Question 6. Which of the following statements about the default route is incorrect?
a) It is specified by an address 0.0.0.0.
b) It is specified by an address 127.0.0.1.
c) It is used for forwarding packets to unknown destinations.
d) None of these.
Question 7. Which of the following routing protocols suffers from the count-to-infinity problem?
a) OSFP
b) BGP
c) RIP
d) None of these
Question 8. Which of the following routing protocols is used for routing between different autonomous systems?
a) RIP
b) OSFP
c) BGP
d) ICMP
Question 9. In Open Shortest Path First (OSPF) routing protocol, which of the following packets is used to check if the neighbor router is up (active)?
a) Link State Request
b) Hello Packet
c) Link State Acknowledgement
d) TCP 3-way handshake
e) None of these
Question 10. Which of the following statement(s) is/are false for IPv6?
a) IPv6 supports address class like A, B, and C.
b) IPv6 addresses are 128-bit long.
c) The base header size in IPv6 is 40 bytes.
d) None of these.
Ethical Hacking Nptel Week 3 Assignment Answers (July-Dec 2024)
Course Link: Click Here
Q1.Which of the following statement(s) is/are false.
a. IP protocol uses connection-oriented routing.
b. IP protocol uses connection-less routing.
C. In connection-less routing, each packet is treated as an independent packet.
d. None of these.
Answer: a. IP protocol uses connection-oriented routing.
Q2.Which of the following is/are false for direct and indirect packet delivery option?
a. Direct delivery occurs when the destination host and deliverer are present on same network.
b. Indirect delivery occurs when the destination host and deliverer are not present on same network.
C. In direct delivery, hosts of same network can exchange packets without interference of router.
d. In an indirect delivery, the packet goes from router to router until it reaches the one connected to the same physical network as its final destination.
e. None of these.
Answer: e. None of these.
For answers or latest updates join our telegram channel: Click here to join
These are Ethical Hacking Nptel Week 3 Assignment Answers 2024
Q3.Which of the following is/are true for dynamic routing?
a. Routes are user defined.
b. Routing table updates periodically depending on the network condition.
c. Routers consume bandwidth for communicating with each other.
d. Failure of the link can be resolved easily (re-routing is easy).
e. None of these.
Answer: b. Routing table updates periodically depending on the network condition. c. Routers consume bandwidth for communicating with each other. d. Failure of the link can be resolved easily (re-routing is easy).
Q4.Which of the following routing flags can indicate route to a single host (and not to a network) in the routing table?
a. U
b. G
c. H
d. D
e. M
Answer: c. H
For answers or latest updates join our telegram channel: Click here to join
These are Ethical Hacking Nptel Week 3 Assignment Answers 2024
Q5.Which of the following statement (s) is/are false for default route?
a. It is used when no specific address for next hop is available.
b. It is specified by an address 0.0.0.0.
c. It is specified by an address 127.0.0.1.
d. None of these.
Answer:c. It is specified by an address 127.0.0.1.
Q6.Which of the following statement(s) is/are true for Routing Information Protocol (RIP)?
a. RIP is an example of interior routing protocol.
b. RIP maintains timers to detect failed links.
c. RIP suffers from counting to infinity problem.
d. RIP allows faster convergence for larger network.
e. None of these.
Answer: a. RIP is an example of interior routing protocol. b. RIP maintains timers to detect failed links. c. RIP suffers from counting to infinity problem.
For answers or latest updates join our telegram channel: Click here to join
These are Ethical Hacking Nptel Week 3 Assignment Answers
Q7.In Open Shortest Path First (OSPF) routing approach, which of the following packets is used to check if the neighbor router is up or not?
a. Link State Request.
b. Link Request Update.
c. Link State Acknowledgement.
d. TCP 3-way handshake.
e. None of these.
Answer: d. TCP 3-way handshake.
Q8.Which of the following is true for IPv6?
a. IPv6 address does not have any defined classes.
b. It uses 128-bit IP addresses.
C. Base header size is 20 byte.
d. IPv6 is connection oriented.
e. All of these.
Answer: a. IPv6 address does not have any defined classes.
b. It uses 128-bit IP addresses.
For answers or latest updates join our telegram channel: Click here to join
These are Ethical Hacking Nptel Week 3 Assignment Answers
Q9.If a packet is to be delivered to all the host in a network, what kind of address should be used to specify the destination?
a. Unicast address.
b. Broadcast address.
c. Anycast address.
d. None of these.
Answer: b. Broadcast address.
Q10.Consider the following routing table in a router. On which interface will an IP packet with destination address 144.25.112.40 be forwarded?
a. Etho
b. Eth1
c. Eth2
d. Eth3
e. Default
Answer: d. Eth3
For answers or latest updates join our telegram channel: Click here to join
These are Ethical Hacking Nptel Week 3 Assignment Answers
More Weeks of Ethical Hacking: Click here
For answers to additional Nptel courses, please refer to this link: NPTEL Assignment Answers
Ethical Hacking Nptel Week 3 Assignment Answers (Jan-Apr 2023)
Course Link: Click Here
These are Ethical Hacking Nptel Week 3 Assignment Answers
Q1. Which of the following statement(s) is/are true?
a. IP protocol uses connection-oriented routing.
b. IP protocol uses connection-less routing.
c. IP protocol is a host-to-host layer.
d. In connection-less routing, each packet is treated as an independent packet. e. None of these.
Answer: b, d
Q2. Which of the following is/are false for direct and indirect packet delivery option?
a. Direct delivery occurs when the destination host and deliverer are not present on same network.
b. Indirect delivery occurs when the destination host and deliverer are present on same network.
c. In direct delivery, hosts of same network can exchange packets without interference of router.
d. In direct delivery, an incoming packet to the router is forwarded to the destination host present in the network.
e. In an indirect delivery, the packet goes from router to router until it reaches the one connected to the same physical network as its final destination.
f. None of these.
Answer: a, b
These are Ethical Hacking Nptel Week 3 Assignment Answers
Q3. Which of the following routing flags can indicate route to a single host (and not to a network) in the routing table?
a. U
b. G
c. H
d. D
e. M
Answer: c. H
Q4. Which of the following statement(s) is/are false?
a. Autonomous systems are set of routers and networks managed by a single organization.
b. In exterior routing protocol, all the participating routers are present in the same autonomous system.
c. In interior routing protocol, the participating routers can be present in different autonomous systems.
d. None of these.
Answer: b, c
These are Ethical Hacking Nptel Week 3 Assignment Answers
Q5. In Open Shortest Path First (OSPF) routing approach, which of the following packets is used to check if the neighbor router is up or not?
a. Link State Request.
b. Link Request Update.
c. Link State Acknowledgement.
d. Using TCP 3-way handshake protocol.
e. None of these.
Answer: e. None of these.
Q6. If a packet is to be delivered to all the hosts in a network, what kind of address should be used to specify the destination?
a. Unicast address.
b. Broadcast address.
c. Anycast address.
d. None of these.
Answer: b. Broadcast address.
These are Ethical Hacking Nptel Week 3 Assignment Answers
Q7. How many bits are used to represent IPv4 and IPv6 addresses respectively?
a. 4, 24
b. 24, 32
c. 32, 64
d. 32, 128
e. 255, 255
Answer: d. 32, 128
Q8. When an entire IPv6 packet is included as payload inside an IPv4 packet, it is called
a. Encapsulation
b. Tunneling
c. Decapsulation
d. None of these
Answer: b. Tunneling
These are Ethical Hacking Nptel Week 3 Assignment Answers
Q9. The size of base header in IPv6 datagram packet is _______ bytes.
Answer: 40
Q10. Consider the following routing table in a router. On which interface will an IP packet with destination address 144.25.112.40 be forwarded?
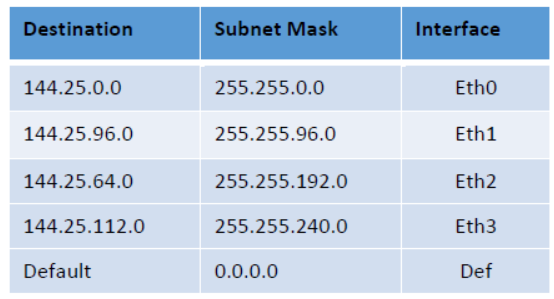
a. Eth0
b. Eth1
c. Eth2
d. Eth3
e. Def
Answer: d. Eth3
These are Ethical Hacking Nptel Week 3 Assignment Answers
More Solutions of Ethical Hacking: Click Here
More NPTEL Solutions: https://progiez.com/nptel-assignment-answers/